How Ransomware-as-a-Service (RaaS) Attacks Have Changed the Game Forever

Ransomware is surging wildly out of control. It seems you can’t even glance at the news today without hearing of another organisation falling victim to a major breach. In 2021, you are currently more likely to be hit by ransomware than not. 84% of organisations have reported a “high concern” incident relating to ransomware in the past 12 months (Osterman Research), with an organisation being successfully attacked every 11 seconds.
As the expansion in ransomware operations continues to grow to a level that was unimaginable even a couple of years ago, this blog takes a look at the reasons behind the surge, the ways in which attack methods have changed significantly in 2021, and what measures your organisation can take to protect itself in the ongoing fight against ransomware.
What is Ransomware-as-a-Service?
The disturbing spike in Ransomware attacks is primarily the result of a dramatic shift from a linear attack model to an insidious, multi-dimensional Ransomware-as-a-Service (Raas) model. The RaaS approach has empowered even the most inexperienced cyber criminals to launch devastatingly successful and sophisticated ransomware attacks across SMEs and larger organisations alike.
Ransomware attack methods are evolving at a faster pace than ever before. Big threats from 2020, like Avaddon, have already been phased out as criminal organisations have moved on to newer, more dangerous threat models. A good example of this is ‘Darkside’, the ransomware from the Darkside Group. It was first seen in August 2020, but was updated to v2.0 in March 2021, and now operates under a Ransomware-as-a-Service (RaaS) model.
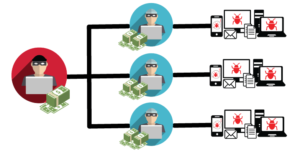 Ransomware as a service (RaaS) is a subscription-based model that enables affiliates to use already-developed ransomware tools to execute devastating attacks. RaaS users don’t need to be skilled or knowledgeable to proficiently use the tools, enabling even the most inexperienced affiliates to execute highly sophisticated cyberattacks and earn substantial dividends from the ransom payments being made.
Ransomware as a service (RaaS) is a subscription-based model that enables affiliates to use already-developed ransomware tools to execute devastating attacks. RaaS users don’t need to be skilled or knowledgeable to proficiently use the tools, enabling even the most inexperienced affiliates to execute highly sophisticated cyberattacks and earn substantial dividends from the ransom payments being made.
Once the ransomware is developed, it’s modified to a multi-end user infrastructure. The software is then ready to be licensed to multiple affiliates using forums across the dark web. The revenue model for RaaS solutions mirrors SaaS products, affiliates can either sign up with a one-time fee or a monthly subscription.
Ransomware affiliates are supported with onboarding documentation containing a step-by-step guide for launching ransomware attacks with the software. Some RaaS distributors even provide affiliates with a dashboard solution to help them monitor the status of each ransomware infection attempt.
The barriers to entry into ransomware operations have been lowered dramatically by RaaS schemes, and this is the main reason why SMEs of all shapes and sizes are now just as much at risk of a ransomware attack as larger organisations and enterprises. Ransomware attacks now target practically every industry, across both the public and private sector, and their intensity continues to grow at an alarming rate.
The number of ransomware ‘threat actors’ is surging dramatically…
The RaaS model has fuelled a humongous influx of more and more ransomware ‘threat actors’ being attracted into the market. ‘Threat Actors’ are the lone agents, organised criminal groups, or entire entities who seek to impact the security of an organisation.
This sharp increase follows a trend already established in 2020 and has led to a huge expansion of existing affiliate schemes and criminal groups. The schemes have significantly increased the revenues of the most established cyber crime groups, which has created a vicious cycle that continues to increase the worldwide expansion in ransomware operations to a level that is hard to comprehend, and as we’ve mentioned right at the start of this post, was previously inconceivable even just a couple of years ago.
How do Ransomware-as-a-Service (Raas) attacks work?
Most ransomware victims are breached through phishing attacks – a method of stealing sensitive data, such as passwords and payment details, through a seemingly innocuous source.
Phishing emails are the most common category of phishing attacks. RaaS affiliates present victims with a very convincing phishing email that seems legitimate. When a link is clicked, victims are unknowingly activating a cyber threat, most often being directed to the exploit site where the ransomware is covertly downloaded.
Once downloaded, the ransomware moves throughout the infected system, disabling firewalls and all antivirus software. After these defences are compromised, the ransomware may trigger the autonomous download of additional remote access components.
 If a vulnerable endpoint is discovered, such as a desktop, laptop, or even IoT device, it could serve as a gateway to the complete internal network of an organisation. Ransomware that surpasses this depth of penetration is capable of holding an entire organisation hostage.
If a vulnerable endpoint is discovered, such as a desktop, laptop, or even IoT device, it could serve as a gateway to the complete internal network of an organisation. Ransomware that surpasses this depth of penetration is capable of holding an entire organisation hostage.
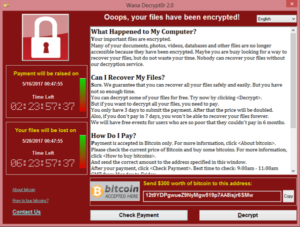
With the ransomware now free to progress without detection, the victim’s files are encrypted to the point of being inaccessible, with most victims being unaware of any data breaches occurring at this point.
After the attack is complete, the extortion game begins. A ransom note is deposited on the victim’s computer instructing them to pay a ransom price in exchange for a decryption key.
What’s the impact of a successful ransomware attack in 2021?
The average cost of ransomware recovery has grown to over £125,000 in the past 12 months (according to Coveware – specialists in negotiating cyber ransom payments), but its impact is more than just that on the bottom line. A breach can also have significant effects on the wellbeing and livelihoods of employees, customers, and other associated stakeholders, not to mention the harm to your brand’s reputation and trust.
A leading stationery firm was hit recently by a major attack (we choose not to name them directly), and one of their senior executives perfectly summed up the substantial consequences of the breach:
I couldn’t believe it when we were hacked, I went into my IT department and the manager was pale and clearly shocked. He told me everything had gone. At one point we actually wrote a press release declaring that the company was dead and out of business. They were the worst three weeks of my life. The hackers demanded we pay them 45 Bitcoin (£1.2m), but in the end, they destroyed so much of our system that we needed to rebuild anyway. Recovering has cost around £500,000.
E-ZU’s Instant ‘Ransomware Risk Calculator’
We highly recommend spending three minutes to assess your organisation’s current ransomware protection level using our Instant Ransomware Risk Calculator. You’ll receive a shareable report that delves deeper into the Ransomware-as-a-Service threat model and how to protect against it, whilst delivering a tailored breakdown of your current ransomware protection level, along with actions and recommendations to address any significant gaps in your defences.
Click the banner below to get started…




